
Encryption is an essential aspect of modern communication and information security. The ability to secure data and prevent unauthorized access has become increasingly important in our digital world. In this article, we will delve into the world of strong cryptographic algorithms, focusing on two widely used algorithms: AES and RSA.
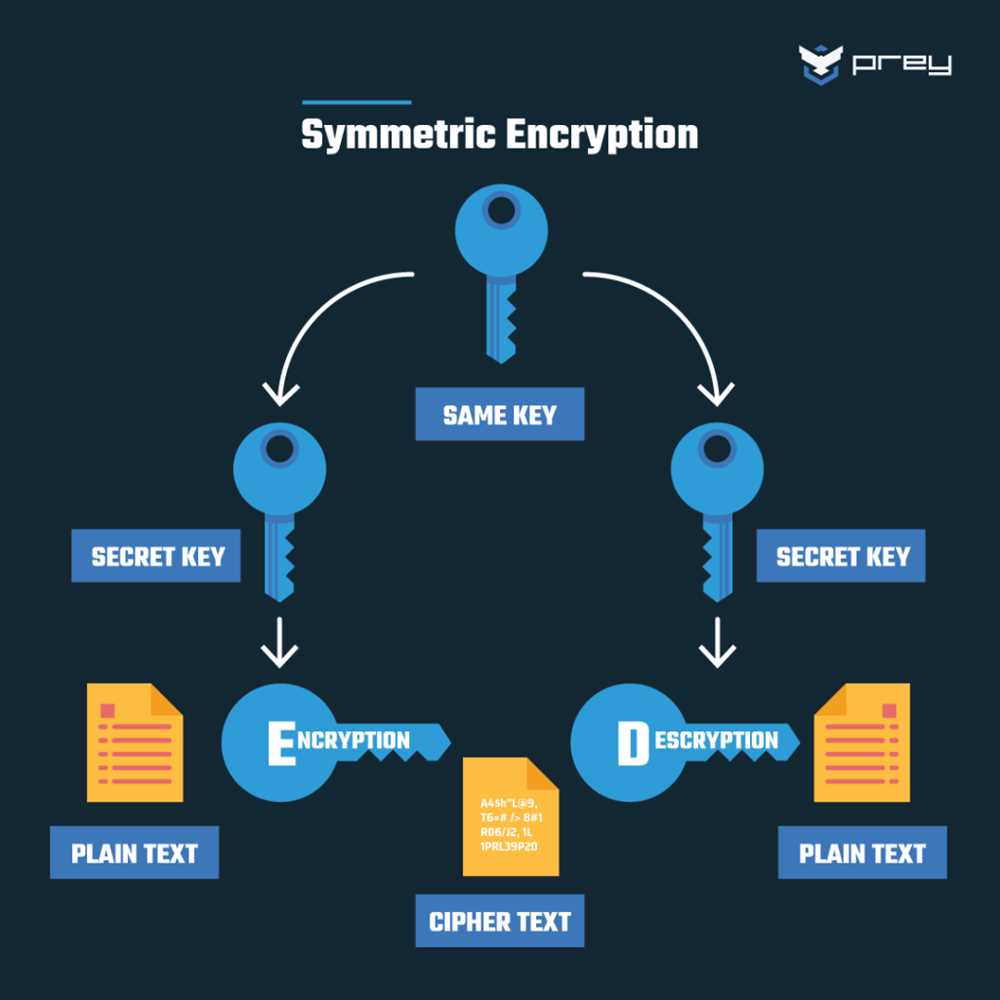
The Advanced Encryption Standard (AES) is a symmetric key encryption algorithm that has been adopted as the standard encryption method by the U.S. government. With AES, the same key is used for both the encryption and decryption processes, making it a fast and efficient algorithm. It employs various key lengths, typically 128, 192, or 256 bits, providing a high level of security.
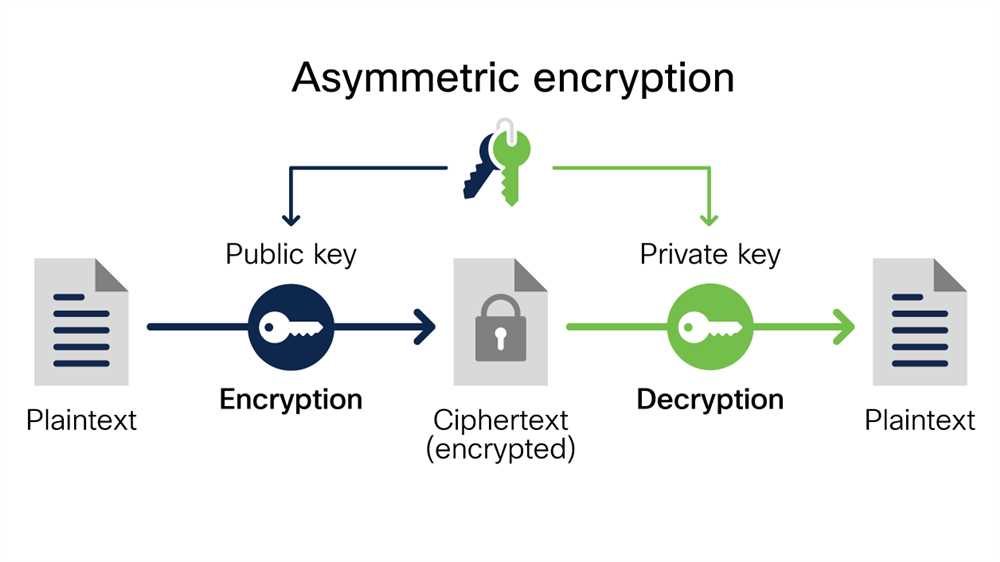
RSA, on the other hand, is an asymmetric key encryption algorithm named after its inventors, Rivest, Shamir, and Adleman. Unlike AES, RSA uses two different keys: a public key for encryption and a private key for decryption. This makes RSA suitable for secure communication and digital signatures. The security of RSA relies on the difficulty of factoring large prime numbers, making it a trusted algorithm for secure data transmission.
Both AES and RSA are widely used in various applications, from securing internet communications to protecting sensitive data in storage. Understanding these powerful cryptographic algorithms is essential for anyone involved in information security. Join us on this exploration of AES and RSA, and discover the fascinating world of strong crypto algorithms.
The Evolution of Cryptographic Algorithms

Cryptographic algorithms have come a long way since their inception. From ancient times when simple ciphers were used to hide messages, to the modern world where advanced encryption techniques provide robust data protection, the evolution of cryptographic algorithms has been remarkable.
Early Encryption
In ancient times, encryption techniques were relatively primitive. Simple substitution ciphers, such as the Caesar cipher, were used to obscure information. These ciphers replaced letters with others in a fixed pattern, making it difficult for unintended recipients to understand the message.
As time went on, more complex ciphers were developed. The Vigenère cipher, for example, used multiple substitution alphabets to further enhance encryption security.
The Rise of Symmetric Algorithms
With the advent of computers, new cryptographic algorithms were developed to meet the growing demand for secure communication and data storage. Symmetric algorithms, such as the Data Encryption Standard (DES), became popular in the 1970s as they provided a fast and efficient way to encrypt and decrypt data.
Rapid advancements in technology led to the development of stronger symmetric algorithms, such as the Advanced Encryption Standard (AES). AES became the gold standard for symmetric encryption due to its high level of security and widespread adoption.
The Birth of Asymmetric Encryption
While symmetric algorithms were effective for many purposes, they relied on both parties sharing the same encryption key, which posed a logistical challenge. As a solution, asymmetric encryption algorithms were invented.
RSA, one of the most widely used asymmetric encryption algorithms, introduced the concept of using a public key for encryption and a private key for decryption. This allowed for secure communication even if the encryption key was known to everyone.
The development of RSA opened up new possibilities for secure communication and authentication on the internet. It paved the way for cryptographic protocols like SSL/TLS, which became the foundation for secure online transactions and communication.
Conclusion
The evolution of cryptographic algorithms has been driven by the need for stronger and more efficient security measures. From ancient encryption methods to modern symmetric and asymmetric algorithms, cryptography has transformed the way we protect sensitive information. As technology continues to advance, we can expect to see further innovation in the field of cryptography, ensuring that our data remains secure in an increasingly interconnected world.
AES: The Strongest Symmetric Encryption
The Advanced Encryption Standard (AES) is widely considered to be the strongest symmetric encryption algorithm currently available. It was published by the National Institute of Standards and Technology (NIST) in 2001 and has since become the de facto standard for symmetric encryption.
AES operates on blocks of data and uses a secret key to carry out the encryption and decryption process. It consists of multiple rounds of simple and well-defined mathematical operations, including substitution, permutation, and XOR. These operations are designed in such a way that the original data is transformed into an encrypted form that is extremely difficult to reverse without the correct key.
The strength of AES lies in its flexibility and security. It supports key sizes of 128, 192, and 256 bits, making it resistant to brute-force attacks. Additionally, it has undergone extensive public scrutiny and analysis, resulting in a widespread consensus on its robustness and resistance to cryptanalysis.
One of the key features of AES is its ability to operate efficiently on a wide range of devices, including computers, smartphones, and even embedded systems. This versatility, combined with its strong encryption capabilities, has made AES the go-to choice for securing sensitive data in a variety of applications, including online banking, e-commerce, and government communications.
Overall, AES is the go-to choice for symmetric encryption due to its strength, flexibility, and widespread adoption. It provides a high level of security while remaining efficient and practical for use in various contexts. As we continue to rely on digital communication and store more sensitive information online, AES plays a crucial role in ensuring the confidentiality and integrity of our data.
RSA: The Pioneering Asymmetric Encryption
RSA, named after its inventors Rivest, Shamir, and Adleman, is one of the pioneering asymmetric encryption algorithms. Introduced in 1978, it revolutionized the field of cryptography by providing a secure method for exchanging encrypted messages without sharing the encryption key.
Unlike symmetric encryption algorithms, which use the same key for both encryption and decryption, RSA employs a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is kept secret and used for decryption. This asymmetric nature of RSA offers several advantages over symmetric encryption methods.
Secure Communication: RSA enables secure communication between two parties without the need for a shared secret key. The sender uses the recipient’s public key to encrypt the message, which can only be decrypted by the recipient using their private key.
Digital Signatures: RSA can also be used for digital signatures. The sender uses their private key to sign a message, and the recipient can verify the signature using the sender’s public key. This ensures the authenticity and integrity of the message.
Key Exchange: RSA can be used for secure key exchange in symmetric encryption schemes. The sender encrypts a randomly generated symmetric key with the recipient’s public key and sends it along with the encrypted message. The recipient can then decrypt the symmetric key using their private key and use it for symmetric encryption and decryption.
Strength and Complexity: RSA is based on the mathematical problem of factoring large composite numbers, which is believed to be difficult and computationally intensive. The security of RSA relies on the difficulty of factoring large numbers. As technology advances, longer key lengths are required to maintain the same level of security.
Standardization and Adoption: RSA has gained widespread adoption and is commonly used in various cryptographic applications, including secure email, SSL/TLS for secure web communication, secure file transfer, and digital certificates.
In conclusion, RSA is a groundbreaking asymmetric encryption algorithm that has revolutionized the field of cryptography. Its unique properties and wide-ranging applications have made it a cornerstone of modern secure communication systems.
Comparing AES and RSA: Strengths and Weaknesses
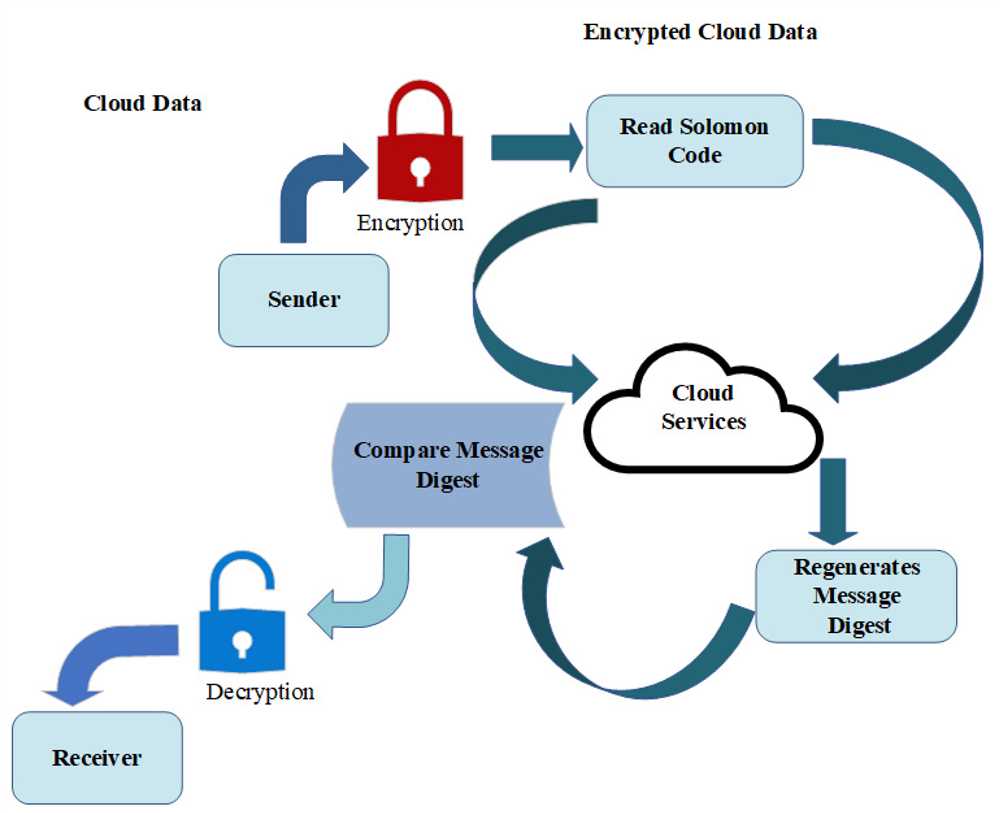
When it comes to strong cryptographic algorithms, AES and RSA are two of the most widely used and respected. Both algorithms provide high levels of security and have their own strengths and weaknesses. Let’s take a closer look at how AES and RSA compare in terms of their strengths and weaknesses.
| Algorithm | Strengths | Weaknesses |
|---|---|---|
| AES | – AES is highly efficient and fast, making it suitable for a wide range of applications. – AES has a long key length options, providing a higher level of security. – AES is resistant to many known cryptographic attacks. |
– AES is a symmetric algorithm, which means the same key is used for both encryption and decryption. This can pose challenges in securely managing and distributing the key. – AES is not suitable for use in applications that require public key encryption. – AES is vulnerable to side-channel attacks, such as timing attacks and power analysis attacks. |
| RSA | – RSA is a widely used public key encryption algorithm, allowing for secure key exchange. – RSA is based on the mathematical problem of factoring large prime numbers, which is believed to be computationally difficult. – RSA can provide both encryption and digital signature capabilities. |
– RSA is generally slower and less efficient compared to symmetric encryption algorithms like AES. – RSA key generation and management can be complex and resource-intensive. – RSA is vulnerable to attacks if the key length is not chosen correctly or if there are implementation flaws. |
In conclusion, both AES and RSA have their own unique strengths and weaknesses. AES is a fast and efficient symmetric encryption algorithm suitable for a wide range of applications but has challenges related to key management and vulnerability to side-channel attacks. RSA, on the other hand, is a widely used public key encryption algorithm that allows for secure key exchange but is generally slower and less efficient compared to AES. As with any cryptographic algorithm, the choice between AES and RSA depends on the specific requirements of the application and the level of security needed.
The Future of Cryptographic Algorithms
As technology continues to advance at an exponential rate, the field of cryptography is also evolving to meet the challenges of an increasingly connected world. The future of cryptographic algorithms promises to be both exciting and complex, with new innovations and discoveries shaping the way we secure our data and communications.
One area that holds great promise is the development of quantum-resistant cryptographic algorithms. As quantum computing becomes more powerful and accessible, the current encryption methods using RSA or AES may no longer be secure. Quantum-resistant algorithms, such as lattice-based or code-based cryptography, are being explored as potential solutions to this problem. These algorithms are designed to withstand attacks from quantum computers, ensuring the long-term security of our data.
Another emerging trend is the use of homomorphic encryption, which allows data to be processed without being decrypted. This enables secure computation on encrypted data, opening up new possibilities for secure cloud computing and data analysis. Homomorphic encryption has the potential to revolutionize the way we handle and protect sensitive information, while still allowing for meaningful analysis and processing.
Furthermore, there is ongoing research in the field of post-quantum cryptography, which focuses on developing encryption algorithms resistant to attacks from both classical and quantum computers. These algorithms aim to provide security in a world where quantum computing is widespread. The exploration of new mathematics, such as multivariate polynomials or isogenies, offers exciting avenues for creating these post-quantum cryptographic algorithms.
While the future of cryptographic algorithms holds great potential, it is important to consider the challenges that come with their implementation. As new algorithms are developed, they must undergo rigorous testing and analysis to ensure their security and effectiveness. Standards organizations and cryptographic researchers play a crucial role in this process by evaluating and validating these algorithms before they are widely adopted.
In conclusion, the future of cryptographic algorithms is a dynamic and evolving field. Quantum-resistant algorithms, homomorphic encryption, and post-quantum cryptography are just a few areas that show promise in securing our data in an increasingly digital world. However, it is important to approach these innovations with caution, ensuring that they are thoroughly tested and validated before widespread implementation.
What is AES?
AES stands for Advanced Encryption Standard. It is a cryptographic algorithm that is widely used for encrypting and decrypting data. AES is considered to be one of the most secure symmetric encryption algorithms.
How does RSA encryption work?
RSA encryption is a public-key encryption algorithm. It works by using two keys – a public key for encryption and a private key for decryption. When someone wants to send a secure message to the owner of the RSA key pair, they use the recipient’s public key to encrypt the message. The recipient can then use their private key to decrypt the message.
What are the differences between AES and RSA?
AES and RSA are both cryptographic algorithms, but they are used for different purposes. AES is a symmetric encryption algorithm, which means it uses the same key for both encryption and decryption. RSA, on the other hand, is an asymmetric encryption algorithm, which uses a different key for encryption and decryption. Additionally, AES is generally faster and more efficient than RSA.
Why is strong encryption important?
Strong encryption is important for ensuring the security and privacy of sensitive information. It helps to protect data from unauthorized access and interception. In today’s digital age, where data breaches and cyber attacks are becoming increasingly common, strong encryption is crucial for individuals, businesses, and governments to safeguard their information.