
As the blockchain industry continues to grow, security remains a top concern for users. TronLink, a popular wallet for the TRON network, takes this concern seriously and has implemented robust security measures to ensure the safest transactions for its users.
One of the key features of TronLink is its strong encryption technology. All sensitive data, such as private keys and seed phrases, are encrypted and stored securely on the user’s device. This means that even if a user’s device is compromised, their private information remains protected.
In addition to encryption, TronLink also utilizes multi-factor authentication to further enhance security. Users can set up additional security measures, such as fingerprint or facial recognition, to ensure that only authorized individuals can access their wallet.
Furthermore, TronLink has implemented a comprehensive auditing system to detect and prevent any malicious activities. This system constantly monitors transactions on the TRON network and flags any suspicious or fraudulent behavior. This ensures that users can have peace of mind knowing that their transactions are being closely scrutinized for any signs of unauthorized activity.
In conclusion, TronLink prioritizes the security of its users’ transactions on the TRON network. Through strong encryption, multi-factor authentication, and a robust auditing system, TronLink ensures that its users can transact with confidence. So if you’re looking for a secure wallet for your TRON transactions, TronLink is a top choice.
About TronLink
TronLink is a secure and user-friendly wallet extension that is designed to provide users with a seamless and secure experience when interacting with the TRON network. Developed by TRON Foundation, TronLink allows users to easily access and manage their TRON assets, participate in decentralized applications (DApps), and execute transactions on the TRON blockchain.
Key Features

- Seamless Integration: TronLink seamlessly integrates with popular web browsers like Chrome, Brave, and Firefox, allowing users to access their TRON assets and interact with DApps directly from their browser without the need to download any additional software.
- Secure Storage: TronLink utilizes state-of-the-art encryption technology to securely store private keys and user data. Private keys are stored locally on the user’s device and are never shared with any third-party servers, ensuring complete control and security over user funds.
- User-Friendly Interface: TronLink provides a clean and intuitive interface that makes it easy for users to navigate and interact with the wallet. Users can easily send and receive TRX and other TRON-based tokens, as well as manage their wallet settings and transactions.
Benefits for TRON Users

TronLink offers a range of benefits for TRON users:
- Secure Transactions: With TronLink, users can confidently execute transactions on the TRON network, knowing that their assets are protected by robust encryption and security measures.
- Convenient Access to DApps: TronLink provides users with easy access to a wide range of decentralized applications on the TRON network. Users can explore and interact with DApps directly from their browser, without the need to create multiple accounts or download separate software.
- Fast and Reliable: TronLink is built with performance in mind, ensuring fast and reliable transactions on the TRON network. Users can enjoy seamless and efficient transaction processing, even during periods of high network activity.
In conclusion, TronLink is a secure and user-friendly wallet extension that offers seamless integration, secure storage, and a user-friendly interface for TRON users. With TronLink, users can confidently and conveniently manage their TRON assets and participate in the thriving ecosystem of decentralized applications on the TRON network.
Importance of Safe Transactions
Safe transactions are of paramount importance in the world of blockchain technology. With the increasing use of digital platforms for financial transactions, security and protection of personal and financial information have become a major concern.
One of the primary reasons for the importance of safe transactions is the need to safeguard against fraudulent activities and unauthorized access to sensitive data. Blockchain technology, by design, provides a transparent and decentralized network where transactions are recorded securely. However, there are still risks associated with online transactions, such as hacking and identity theft.
Protecting Financial Assets
Safe transactions ensure that individuals and businesses can protect their financial assets. By using secure platforms like TronLink, users can mitigate the risk of losing funds and ensure that their transactions are conducted safely. This is particularly crucial in the context of the TRON network, where the value of TRX and other digital assets can fluctuate.
TronLink provides users with a secure wallet that allows them to store, send, and receive TRX and other digital tokens safely. By utilizing encryption and authentication techniques, TronLink ensures that users have full control and ownership of their funds.
Building Trust and Confidence
Safe transactions also contribute to building trust and confidence in the TRON network. When users know that their transactions are secure and protected, they are more likely to engage in financial activities and interact with decentralized applications (dApps) with peace of mind.
Additionally, safe transactions help prevent fraudulent activities within the TRON ecosystem. By implementing robust security measures, TronLink minimizes the risk of scams, phishing attempts, and other malicious activities. This fosters a safer environment for users to participate in the TRON network.
In conclusion, safe transactions are essential for individuals and businesses operating within the TRON network. TronLink plays a crucial role in ensuring the security of transactions, protecting financial assets, and building trust among users. By prioritizing safety and security, TronLink contributes to the sustainable growth and development of the TRON ecosystem.
Secure Wallet Integration
In order to ensure the safest transactions on the TRON network, TronLink prioritizes secure wallet integration. TronLink has partnered with leading wallet providers to provide users with a seamless and secure experience.
Through secure wallet integration, TronLink allows users to securely manage their TRON assets and interact with decentralized applications (DApps) on the TRON network. By integrating with trusted wallet providers, TronLink ensures that users can confidently store and transfer their TRON tokens without the risk of loss or theft.
TronLink supports integration with a variety of wallets, including hardware wallets like Ledger and Trezor. These hardware wallets provide an extra layer of security by keeping users’ private keys offline and protected from potential cyber attacks. With hardware wallet integration, users can securely access their TRON assets and authorize transactions with peace of mind.
In addition to hardware wallets, TronLink also integrates with various software wallets, including mobile wallets like Trust Wallet and desktop wallets like TronScan. These wallets provide a convenient way for users to access their TRON assets while maintaining a high level of security. With software wallet integration, users can easily manage their TRON tokens and interact with DApps on the TRON network from their preferred device.
By prioritizing secure wallet integration, TronLink ensures that users can confidently transact on the TRON network without worrying about the safety of their funds. Whether using a hardware wallet or a software wallet, TronLink provides a seamless and secure experience for managing TRON assets and interacting with the TRON ecosystem.
| Hardware Wallets | Software Wallets |
|---|---|
| Ledger | Trust Wallet |
| Trezor | TronScan |
Strong Encryption
TronLink ensures the safest transactions on the TRON Network through strong encryption. By using advanced encryption algorithms, TronLink encrypts all user data, including private keys and transaction information, to protect against unauthorized access and potential security threats.
The encryption process used by TronLink follows industry best practices and standards, ensuring that user information remains secure and confidential. TronLink employs strong cryptographic algorithms, such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), to protect sensitive data and ensure its integrity throughout the transaction process.
In addition to encryption, TronLink also implements secure key management practices. Private keys are stored locally on the user’s device and are never transmitted over the network, further reducing the risk of unauthorized access. TronLink also supports hardware wallet integration, providing an additional layer of security for users who prefer to store their private keys on a separate device.
Furthermore, TronLink regularly updates its encryption algorithms and security protocols to stay ahead of emerging threats. By constantly monitoring and improving its security measures, TronLink aims to provide users with the highest level of protection when transacting on the TRON Network.
In summary, TronLink’s strong encryption ensures that user data and transactions are safeguarded against potential security risks. Through advanced encryption algorithms, secure key management practices, and regular updates, TronLink prioritizes the safety and security of its users on the TRON Network.
Biometric Authentication
TronLink ensures the safest transactions on the TRON network through the use of biometric authentication. Biometric authentication is a security measure that verifies a user’s identity based on their unique biological characteristics, such as fingerprints, facial recognition, or iris scans.
By incorporating biometric authentication into the TronLink platform, users can securely access their accounts and authorize transactions without the need for passwords or traditional authentication methods. This not only enhances the user experience but also provides an added layer of security, as biometric data is difficult to replicate or forge.
TronLink’s biometric authentication uses advanced algorithms and secure encryption to ensure the privacy and integrity of user biometric data. The data is stored locally on the user’s device and is never transmitted over the internet, further minimizing the risk of unauthorized access.
With biometric authentication, TronLink ensures that only authorized individuals can access and initiate transactions on the TRON network, reducing the likelihood of fraud or unauthorized activity. This enhances trust and confidence in the platform, making it a preferred choice for users looking for secure and convenient transactions on the TRON network.
Backup and Recovery

Ensuring the safety of your TRON transactions is of utmost importance. That’s why TronLink provides a reliable backup and recovery feature to safeguard your funds.
With the backup and recovery feature, it’s easy to back up your TronLink wallet and restore it if needed. This ensures that even if you lose your device or it gets damaged, you can still retrieve your funds without any hassle.
To back up your TronLink wallet, simply follow these steps:
- Open TronLink on your device.
- Access the settings menu.
- Click on the “Backup Wallet” option.
- Follow the on-screen instructions to create a backup.
It’s recommended to store your backup in a secure location, such as an encrypted external hard drive or a password-protected cloud storage service.
If you ever need to recover your wallet, here’s what you should do:
- Install TronLink on your new device or the device you want to recover your wallet on.
- Access the settings menu.
- Click on the “Recover Wallet” option.
- Follow the on-screen instructions to restore your wallet using the backup file.
It’s crucial to keep your backup file and recovery phrase in a safe and secure place, separate from your device. This ensures that even if your device is compromised, you can still recover your wallet and funds.
Additional Security Measures
TronLink also offers additional security measures to protect your wallet. These include:
- Passcode Lock: Set a passcode lock for your TronLink app to prevent unauthorized access.
- Biometric Authentication: Use biometric authentication, such as fingerprint or face recognition, to unlock your TronLink app.
- Two-Factor Authentication (2FA): Enable 2FA to add an extra layer of security to your TronLink account.
By taking advantage of these security measures and regularly backing up your TronLink wallet, you can ensure the safest transactions on the TRON network.
Transaction Verification
TronLink takes transaction verification seriously to ensure the safest transactions on the TRON network. Every transaction made through TronLink goes through a rigorous verification process to confirm its integrity and authenticity.
When a user initiates a transaction using TronLink, it is first encrypted and securely transmitted to the TRON network. The transaction is then verified by multiple nodes on the network to ensure that it follows the proper protocol and meets all the necessary requirements.
During the verification process, TronLink checks various aspects of the transaction, including the source and destination addresses, transaction amount, and any additional data attached to the transaction. This comprehensive verification helps to prevent any potential fraud or malicious activity on the TRON network.
TronLink also employs cryptographic techniques to ensure the security and integrity of every transaction. These techniques use complex algorithms to encrypt and decrypt the transaction data, making it virtually impossible for any unauthorized parties to intercept or modify the transaction.
Furthermore, TronLink utilizes a decentralized system for transaction verification. This means that the transaction is not confirmed by a single centralized authority, but by multiple nodes spread across the TRON network. This decentralized approach adds an extra layer of security and ensures that the transaction is validated by a consensus of trusted nodes.
In summary, TronLink’s transaction verification process is designed to guarantee the safety and reliability of transactions on the TRON network. Through encryption, multiple node verification, and a decentralized system, TronLink ensures that every transaction is secure, trustworthy, and protected against any potential threats.
Smart Contract Auditing
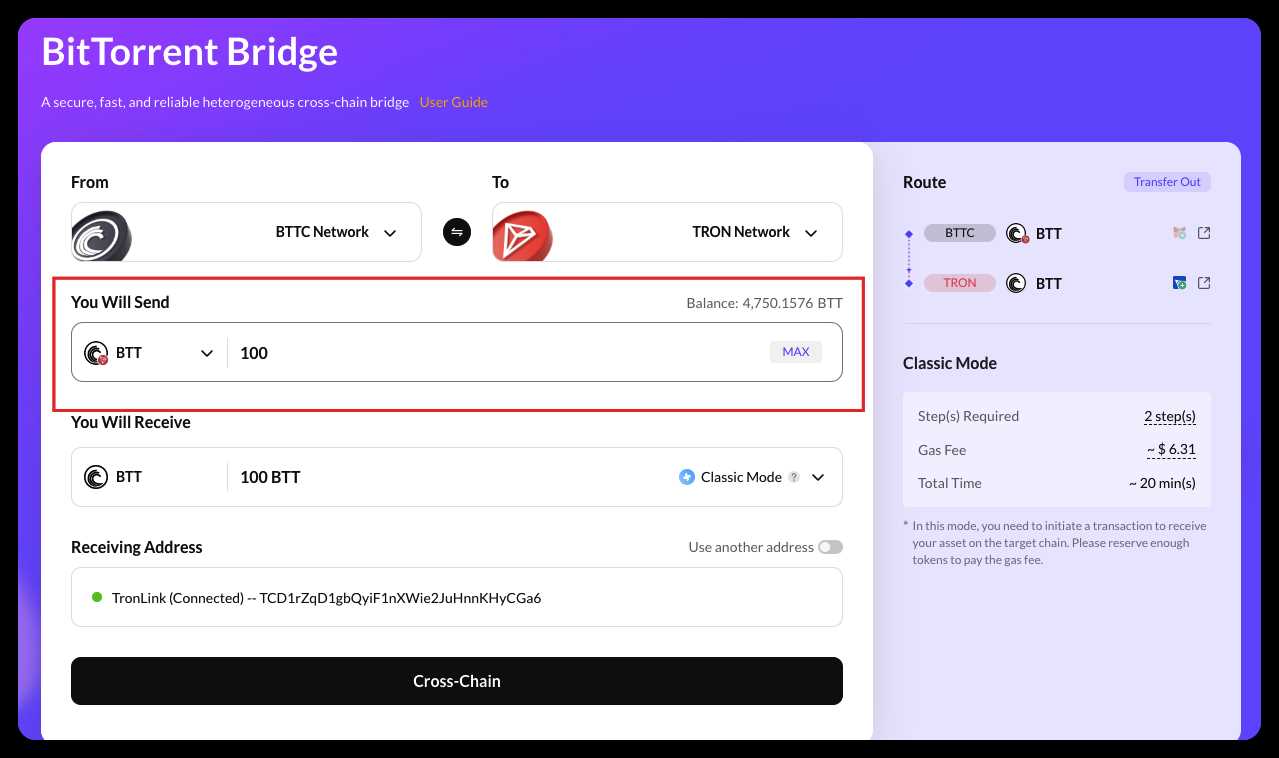
Smart contracts are an integral part of the TRON network, allowing for the execution of decentralized applications (dApps) and facilitating transactions. However, smart contracts are not immune to vulnerabilities and can be subject to various types of attacks. To ensure the safety and security of transactions on the TRON network, TronLink conducts thorough smart contract auditing.
What is Smart Contract Auditing?
Smart contract auditing is a process of reviewing and analyzing the code of a smart contract to identify any flaws, vulnerabilities, or potential risks. Through careful examination, auditors can identify potential security vulnerabilities and suggest improvements to enhance the integrity and security of the smart contract.
During the auditing process, auditors analyze the code structure, logic, and potential risks associated with the smart contract. They look for common vulnerabilities such as reentrancy, integer overflow, or external call vulnerabilities. Additionally, auditors also evaluate the overall design and functionality of the smart contract, ensuring it aligns with its intended purpose and meets industry best practices.
By conducting smart contract auditing, TronLink aims to provide a secure environment for users to interact with the TRON network and dApps. It helps in minimizing the risks of potential attacks, vulnerabilities, and loss of user funds.
TronLink’s Smart Contract Auditing Process
TronLink follows a comprehensive auditing process to ensure the safety of transactions on the TRON network. This process involves the following steps:
| Step | Description |
|---|---|
| 1 | Code Review: Auditors carefully review the smart contract code to identify any flaws or vulnerabilities. |
| 2 | Risk Assessment: Auditors assess the potential risks and impact associated with identified vulnerabilities. |
| 3 | Testing: Auditors conduct extensive testing to validate the functionality and security of the smart contract. |
| 4 | Report and Recommendations: Auditors provide a detailed report outlining the identified vulnerabilities and recommendations for improvements. |
| 5 | Implementation of Recommendations: TronLink addresses the identified vulnerabilities by implementing the recommendations provided by auditors. |
By following this rigorous auditing process, TronLink ensures that the smart contracts deployed on the TRON network are secure and reliable, safeguarding user transactions and assets.
Address Whitelisting

In order to ensure the safest transactions on the TRON network, TronLink offers a feature called Address Whitelisting. This feature allows users to create a whitelist of addresses that are considered safe for transactions.
When a user enables Address Whitelisting, only transactions to and from the addresses on the whitelist will be allowed. This greatly reduces the risk of sending or receiving funds to or from malicious or fraudulent addresses.
How to Enable Address Whitelisting

- Open the TronLink application on your device.
- Go to the settings menu.
- Find the option for Address Whitelisting and toggle it on.
- A list of addresses will be displayed, allowing you to add or remove addresses from the whitelist.
- Once you have added the desired addresses, ensure that the whitelist is saved.
Benefits of Address Whitelisting
Address Whitelisting offers several benefits to users, including:
- Enhanced security: By limiting transactions to only trusted addresses, the risk of falling victim to malicious activities is significantly reduced.
- Preventing accidental transactions: Whitelisting ensures that funds can only be sent to and received from approved addresses, eliminating the possibility of accidentally sending funds to the wrong address.
- Peace of mind: Users can have peace of mind knowing that their transactions are being conducted with trusted parties.
Address Whitelisting is a powerful tool in ensuring the safety of transactions on the TRON network. By utilizing this feature, users can protect themselves from potential scams and fraudulent activities while enjoying the benefits of the decentralized TRON ecosystem.
Two-Factor Authentication
TronLink ensures the safest transactions on the TRON Network by implementing a strong two-factor authentication (2FA) system. This additional layer of security helps protect users’ accounts from unauthorized access and ensures that only the account owner can perform transactions.
TronLink’s 2FA method requires users to provide two pieces of information to verify their identity:
- Something you know: Users are required to provide a unique password that only they know. This password should be strong and kept confidential to prevent unauthorized access.
- Something you have: TronLink also supports the use of hardware wallets, such as Ledger or Trezor, for authentication. These wallets act as a physical device that the user possesses and can be used to confirm transactions securely.
By combining these two factors, TronLink ensures that users’ accounts are well-protected and significantly reduces the risk of unauthorized access or fraudulent activity. This added security measure gives peace of mind to TronLink users and allows them to transact on the TRON Network with confidence.
Protection Against Phishing Attacks
TronLink takes the security of its users seriously and has implemented various measures to protect them against phishing attacks.
Phishing attacks are malicious attempts to deceive users into revealing their sensitive information, such as passwords or private keys, by impersonating a legitimate website or service. TronLink employs several strategies to combat these attacks:
1. Two-Factor Authentication (2FA): TronLink supports 2FA, which adds an extra layer of security by requiring users to enter a code from their mobile device in addition to their password. This ensures that even if an attacker has obtained a user’s password, they still cannot access their TronLink account without the 2FA code.
2. Secure Connection: TronLink uses secure HTTPS connections to ensure that all communication between the user’s device and the TronLink servers is encrypted and protected from eavesdropping or tampering.
3. Anti-Phishing Measures: TronLink actively monitors for phishing attempts and employs filters and other detection mechanisms to identify and block known phishing websites. In addition, TronLink educates its users on how to recognize and avoid phishing attacks through educational materials and security alerts.
4. Account Recovery: In the unfortunate event that a user falls victim to a phishing attack and loses access to their TronLink account, TronLink provides an account recovery process. This process involves a series of verification steps to ensure that the rightful account owner regains access while protecting against unauthorized access.
5. Community Reporting: TronLink encourages its community members to report any suspicious activities or phishing attempts they come across. By leveraging the collective vigilance of its user base, TronLink can quickly identify and mitigate new phishing threats.
By implementing these measures, TronLink aims to provide its users with the safest possible environment for conducting transactions on the TRON network, protecting their assets and sensitive information from phishing attacks.
URL Validation
In order to ensure the safest transactions on the TRON network, TronLink implements a rigorous URL validation system. This system is designed to verify the validity and security of the URLs that users interact with while using TronLink.
Why URL Validation is Important

URL validation plays a crucial role in protecting users from phishing attacks and other malicious activities. By validating URLs, TronLink can help users identify and avoid potentially harmful websites or applications that may attempt to compromise their security.
Phishing attacks are a common method used by cybercriminals to trick users into revealing sensitive information, such as passwords or private keys. These attacks often involve creating fake websites or applications that mimic legitimate ones, making it difficult for users to distinguish between the two.
Through URL validation, TronLink can help users differentiate between legitimate and fake URLs. This helps prevent users from unknowingly accessing malicious websites or applications, reducing the risk of falling victim to phishing attacks.
How URL Validation Works
TronLink’s URL validation system involves several key steps:
- URL Parsing: TronLink parses the URL provided by the user and breaks it down into its components, such as the protocol, hostname, and path.
- Domain Verification: TronLink verifies the authenticity of the domain name associated with the URL. It checks for domain ownership, validity, and other factors to ensure that the domain is not associated with any suspicious or malicious activities.
- HTTPS Protocol: TronLink ensures that the URL is secured with the HTTPS protocol. This protocol encrypts the data exchanged between the user’s browser and the website, providing an additional layer of security.
- Certificate Validation: TronLink validates the SSL certificate of the website, ensuring that it is issued by a trusted certificate authority and has not been tampered with. This helps establish the authenticity and security of the website.
- Phishing Database: TronLink compares the URL against a constantly updated phishing database. If a match is found, TronLink warns the user about the potential risk associated with the URL.
By performing these validation checks, TronLink strives to provide users with a secure environment for conducting transactions on the TRON network. It allows users to confidently interact with URLs through TronLink, knowing that they are protected from potential threats.
Anti-phishing Warnings
TronLink takes the security of your transactions on the TRON network seriously. In order to protect users from phishing attempts, TronLink has implemented strong anti-phishing measures.
When you use TronLink, you may encounter websites or applications that try to trick you into revealing your private keys or other sensitive information. These phishing attempts can lead to significant losses and compromise the security of your TRON assets.
To prevent phishing attacks, TronLink utilizes anti-phishing warnings. When you visit a suspicious website or application, TronLink will display a warning to alert you of the potential danger. This warning serves as a reminder to be cautious and stay vigilant to protect your assets.
It is important to pay attention to these warnings and only interact with trusted websites and applications. TronLink recommends verifying the authenticity of the website or application before proceeding with any transactions or entering any sensitive information.
In addition to the anti-phishing warnings, TronLink also provides education and resources to help users identify and avoid phishing attempts. By staying informed and educated, you can significantly reduce the risk of falling victim to a phishing attack.
Remember, always prioritize the security of your TRON assets. With TronLink’s anti-phishing warnings and your own cautiousness, you can ensure the safest transactions on the TRON network.
Secure Login Procedures

TronLink takes security seriously and has implemented a series of secure login procedures to ensure the safest transactions on the TRON network.
When you first download and install TronLink, you will need to create a secure password. This password should be unique and not used for any other accounts. TronLink also encourages the use of a strong password with a combination of uppercase and lowercase letters, numbers, and special characters.
After creating your password, TronLink will generate a unique 12-word mnemonic phrase that serves as a backup to your account. It is essential to write down and store this phrase in a safe place as it can be used to restore your account in case of loss or theft of your device.
When logging into your TronLink account, you will be prompted to enter your password. Additionally, TronLink offers two-factor authentication (2FA) as an added layer of security. You can enable 2FA by linking your account to an authenticator app such as Google Authenticator.
TronLink also supports biometric authentication, such as fingerprint or facial recognition, on compatible devices. This provides an extra level of security when logging in to your account.
In addition to these login procedures, TronLink regularly updates its software to fix any security vulnerabilities and protect against potential threats. It is crucial to keep your TronLink app up to date to ensure you have the latest security features and protections.
By following these secure login procedures, TronLink ensures that your transactions on the TRON network are protected and your account remains secure.
FAQ:
Why is TronLink considered one of the safest ways to transact on the TRON network?
TronLink is considered one of the safest ways to transact on the TRON network because it utilizes state-of-the-art security measures, such as encrypted private keys, to protect user funds. Additionally, TronLink does not store user information or private keys, further enhancing security.
How does TronLink protect against unauthorized access to user accounts?
TronLink protects against unauthorized access to user accounts through the use of encrypted private keys, which are stored locally on the user’s device. The private keys are never transmitted over the internet, ensuring that only the user has access to their account and funds.
Does TronLink support multi-signature transactions?
Yes, TronLink supports multi-signature transactions. This feature allows multiple parties to sign off on a transaction before it is executed, providing an extra layer of security and ensuring that all parties involved in the transaction agree to its terms.
What happens if a user loses their TronLink wallet?
If a user loses their TronLink wallet, they can easily recover their account by using the recovery phrase provided during the initial setup. By entering the recovery phrase into a new TronLink wallet, the user can regain access to their account and funds.
Can TronLink be used for decentralized applications (DApps) on the TRON network?
Yes, TronLink can be used for decentralized applications on the TRON network. TronLink provides a seamless integration with DApps, allowing users to easily interact with and transact on various DApps without compromising their security or privacy.